Analyzing AMD SEV's Remote Attestation
By Franziskus Kiefer
From 19:30 to 22:00
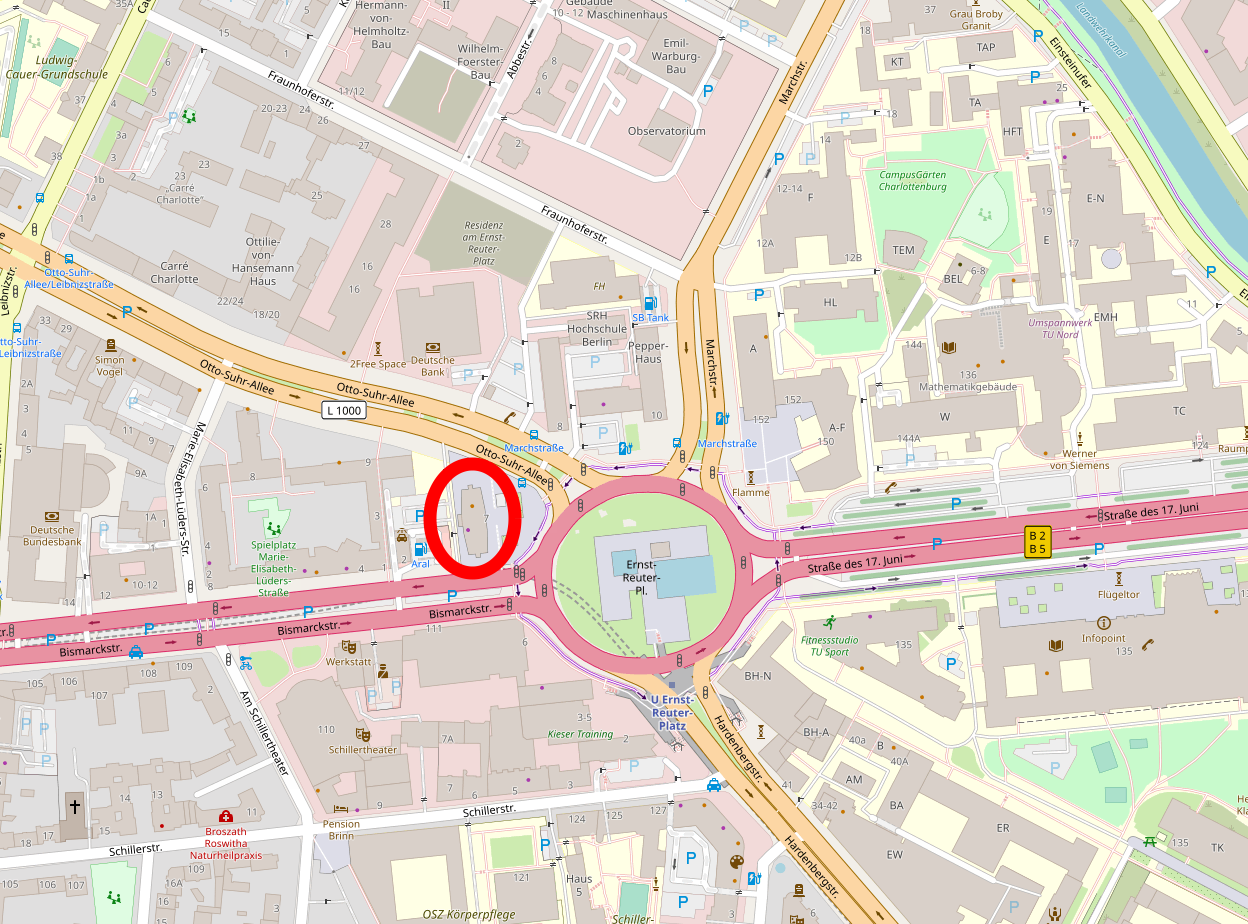
TU Berlin/T-Labs, Ernst-Reuter-Platz 7, 10587 Berlin
TEL building, 20th floor, Room AUDI 3
After a short holiday break and a lazy January the Berlin Crypto meetup is back with a talk on how to attack the AMD SEV remote attestation. In an increasingly cloud-based world cryptography is used to secure virtual machines running in untrusted environments. Robert will show us how to attack such a seemingly secure system.
Come and join our community of Berliners interested in everything around cryptography! Doors will open at 19:30. There will be Robert’s talk and plenty of time to socialise and discuss any issues of interest.
Insecure Until Proven Updated - Analyzing AMD SEV’s Remote Attestation (Robert Buhren)
Cloud computing is one of the most prominent technologies to host Internet services that unfortunately leads to an increased risk of data theft. AMD Secure Encrypted Virtualization (SEV) claims a new level of protection in such cloud scenarios. AMD SEV encrypts the main memory of virtual machines with VM-specific keys, thereby denying the higher-privileged hypervisor access to a guest’s memory. To enable the cloud customer to verify the correct deployment of his virtual machine, SEV additionally introduces a remote attestation protocol. This protocol is a crucial component of the SEV technology that can prove that SEV protection is in place and that the virtual machine was not subject to manipulation.
The remote attestation protocol is implemented on a dedicated security subsystem, the “Platform-Security-Processor” (PSP). The PSP is an ARM CPU embedded in AMD’s x86 CPUs, hosting firmware provided by AMD. This talk presents the result of our security analysis of the PSP.
The talk is based on the CCS 2019 paper Insecure Until Proven Updated: Analyzing AMD SEV’s Remote Attestation.
Get slides (pdf)
Location: TEL building, 20th floor, Room AUDI 3
 Berlin Crypto
Berlin Crypto